iOS 18.1 Security Feature: Inactivity Rebooting
A new security feature introduced in iOS 18 puzzled police departments in the US. iPhones seemed to magically reboot without any input by the officers. What is actually happening here? Is this good for the user and was it an intended update?

It has been a while since we last heard about iPhones mysteriously rebooting. First it was a bug present in iOS 18 for the new iPhone 16 lineup where it would crash the phone up to 20 times a day. This, on the other hand, is a planned feature that boosts the security of the iPhone significantly, as it somewhat addresses a large problem that has been plaguing smartphone security for a long time. But does this affect you? Is this even a positive change?
What happened?
On the 7th of November, 404 Media reported that iPhones running the latest iOS 18 version had started rebooting for no apparent reason. The way they found this out was quite interesting, though. They managed to get a hold of a police document warning other law enforcement that iPhones could start rebooting when sat in storage, thus effectively locking them out from getting any data. The notice read the following, which we will dissect later, so don’t worry too much about any unknown terms or concepts:
The purpose of this notice is to spread awareness of a situation involving iPhones, which is causing iPhone devices to reboot in a short amount of time (observations are possibly within 24 hours) when removed from a cellular network. If the iPhone was in an After First Unlock (AFU) state, the device returns to a Before First Unlock (BFU) state after the reboot. This can be very detrimental to the acquisition of digital evidence from devices that are not supported in any state outside of AFU.
It is believed that the iPhone devices with iOS 18.0 brought into the lab, if conditions were available, communicated with the other iPhone devices that were powered on in the vault in AFU. That communication sent a signal to devices to reboot after so much time had transpired since device activity or being off network.
Did this have anything to do with the fault that caused the recently released iPhones to reboot? Or was this unrelated? For now, the officers didn’t have a clear idea of what was happening, only a clue to act fast when searching iPhones.
So what did this actually mean?
If you haven’t looked into this before, all of this might be slightly confusing. Behind this, there is a basic concept however: the BFU and AFU state your iPhone can be in.
The BFU (Before first unlock) state is only active if, after a reboot, you haven’t already unlocked your phone. In this case, no data on the phone can be accessed, everything is still encrypted.
Only when you first unlock your phone, does it reach AFU (After first unlock) status. That is also a reason why FaceID doesn’t work right after rebooting your phone, the information necessary simply cannot be accessed. After entering the passcode, the decryption keys are loaded into memory so everything works as you expect and all data is accessible.
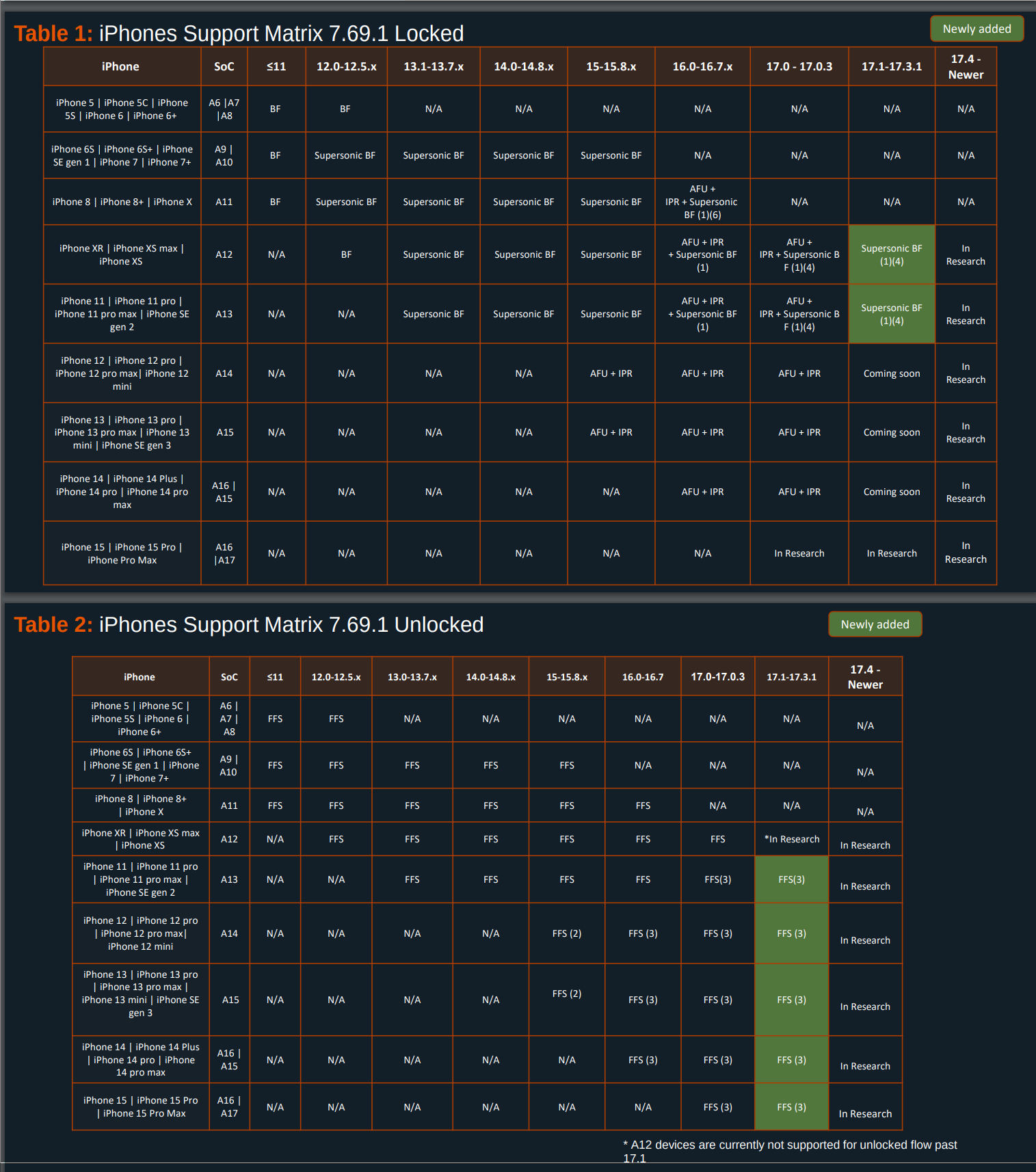
The difference here are the encryption keys. After the first unlock, they are in memory. While all of this is a gross oversimplification (we don’t actually want to go into the very fine details, they are also incredibly difficult to find), the keys can be extracted more easily (or even at all) in this state because they must be stored unencrypted in memory. As illustrated by the screenshot below, a commercially available tool to unlock and extract data from phones called Cellebrite lists many crackable iPhones as only being supported in the AFU state. There is much more information there as well, but what is important for now, is the difference an AFU and BFU status makes. As an additional explanation: Supersonic BF stands for supersonic brute-force, a way of saying the passcode (the PIN you set) can be found out via extremely fast trial-and error, bypassing the waiting timer after guessing wrong several times. This only works on older models, though, and we don’t have any more leaked information about iOS 17.4 or newer. Nonetheless, this should give a good overview of why a BFU state can be indispensable if you don’t want your data stolen.
Are the police the bad actors here?
This article isn’t supposed to blame the police directly for wanting to access data from iPhones. While there can certainly be searches that are not warranted, laws often explicitly allow this kind of search. So it is challenging to argue against the police for using a legally permissible piece of evidence.
While I’m personally not a friend of this kind of data extraction, criminals that stole your phone could possibly also gather data from it in the same way. And there I think we can all agree that this isn’t good for anyone. In addition to having your expensive phone stolen, your identity, banking information etc. would all be present, enabling blackmail for example.
Because of this, it would be an excellent feature if your phone, when it isn’t used for a long time, could revert to a BFU state, making it (at least for now) almost impossible to unlock without knowing the code. And for you, this only means that you need to enter your unlock code once more.
A resolution to the puzzle
Only a day after this went down, 404 Media released another report that this a feature that has been introduced by Apple to strengthen the iPhone’s security. They haven’t announced this publicly, it has only been found by the police inadvertently and confirmed by a security researcher. Because of this information, we can conclude that iPhones aren’t communicating with each other for this purpose or even using location-based hints. Instead, a check happens that looks for the last time the phone has been unlocked. If this point is more than 72 hours ago, the phone will reboot.
So far, Apple hasn’t commented on this, but it has been identified as a planned feature, so we can assume it is here to stay.
Is this good or bad for the user?
As already mentioned, for the user this is an excellent feature for improving your iPhone’s security. Occasionally, you already have to enter your passcode instead of just using FaceID for security reasons. If you haven’t touched your phone in a few days, you likely won’t mind having to enter the code once more. For that small price, criminals (which seem to be the intended threat actor here) will have a much harder time accessing your personal information should your iPhone ever be stolen. Now let’s just hope that never happens to begin with.
This article is published under the CC BY-SA 4.0 license.